Navigating the Shadows: Understanding TOR
Introduction: Why Use TOR?
TOR, or The Onion Router, is a specialized web browser designed for anonymity and privacy. Unlike standard browsers, TOR obscures a user's IP address and location, making it an essential tool for those in restrictive countries, journalists, activists, and privacy-conscious users.
How Does TOR Work?
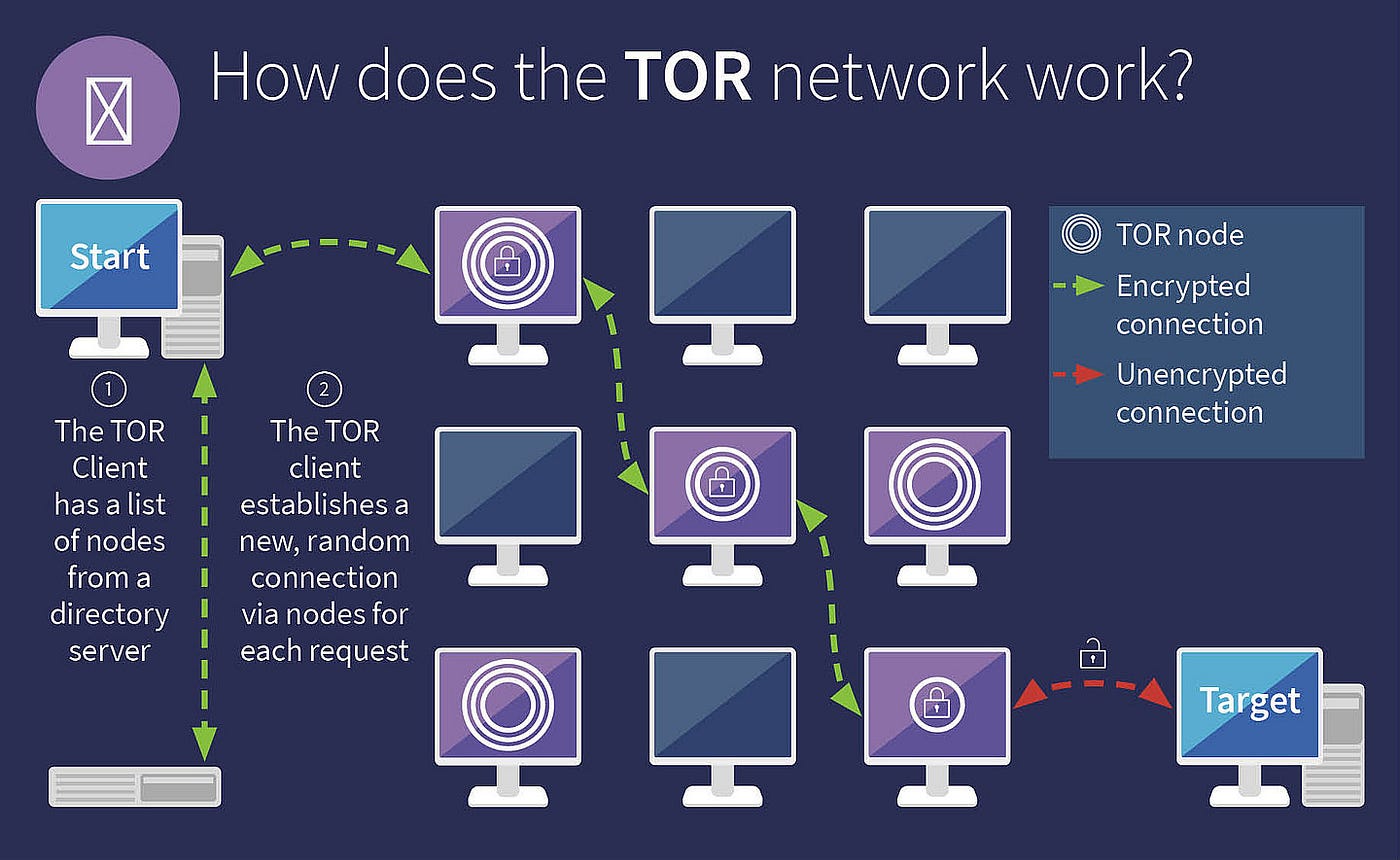
TOR ensures privacy through a complex network of volunteer-run servers known as nodes. Here's how it functions:
Clients and Nodes
- Role of Nodes: Users' data passes through multiple nodes in the TOR network. Each node knows only the IP of the node before and after it, maintaining user anonymity.
- Path of Data: The data journey starts at the user (the client), moves through several intermediate nodes, and finally exits the network to reach the intended destination.
Encrypted and Unencrypted Connections
- Encryption Layers: Data is layered with encryption, each layer decrypted by a successive node, resembling the layers of an onion.
- Exit Node Vulnerability: The final node decrypts the last layer. If the destination website is not using HTTPS, the data from this point is unencrypted.
Using TOR Safely
To maximize TOR's effectiveness and safety:
- Use a VPN: A Virtual Private Network (VPN) should accompany TOR, adding an extra security layer and obscuring TOR usage from ISPs.
- Browse Wisely: Users must avoid unsafe practices like downloading unknown files or enabling plugins.
Anonymity on the Dark Web
While TOR offers access to the dark web, it doesn't provide absolute anonymity:
- VPN Importance: A VPN hides TOR usage from ISPs, enhancing anonymity.
- ISP and Government Tracking: ISPs can detect TOR usage and may cooperate with authorities in suspicious cases.
- Limits of Anonymity: While TOR makes tracking difficult, it's not impossible, especially for advanced adversaries like government agencies.
Conclusion
TOR is a powerful tool for online privacy and censorship circumvention, but it's not infallible. Users should combine TOR with a VPN and practice cautious browsing to maximize their online security and privacy.